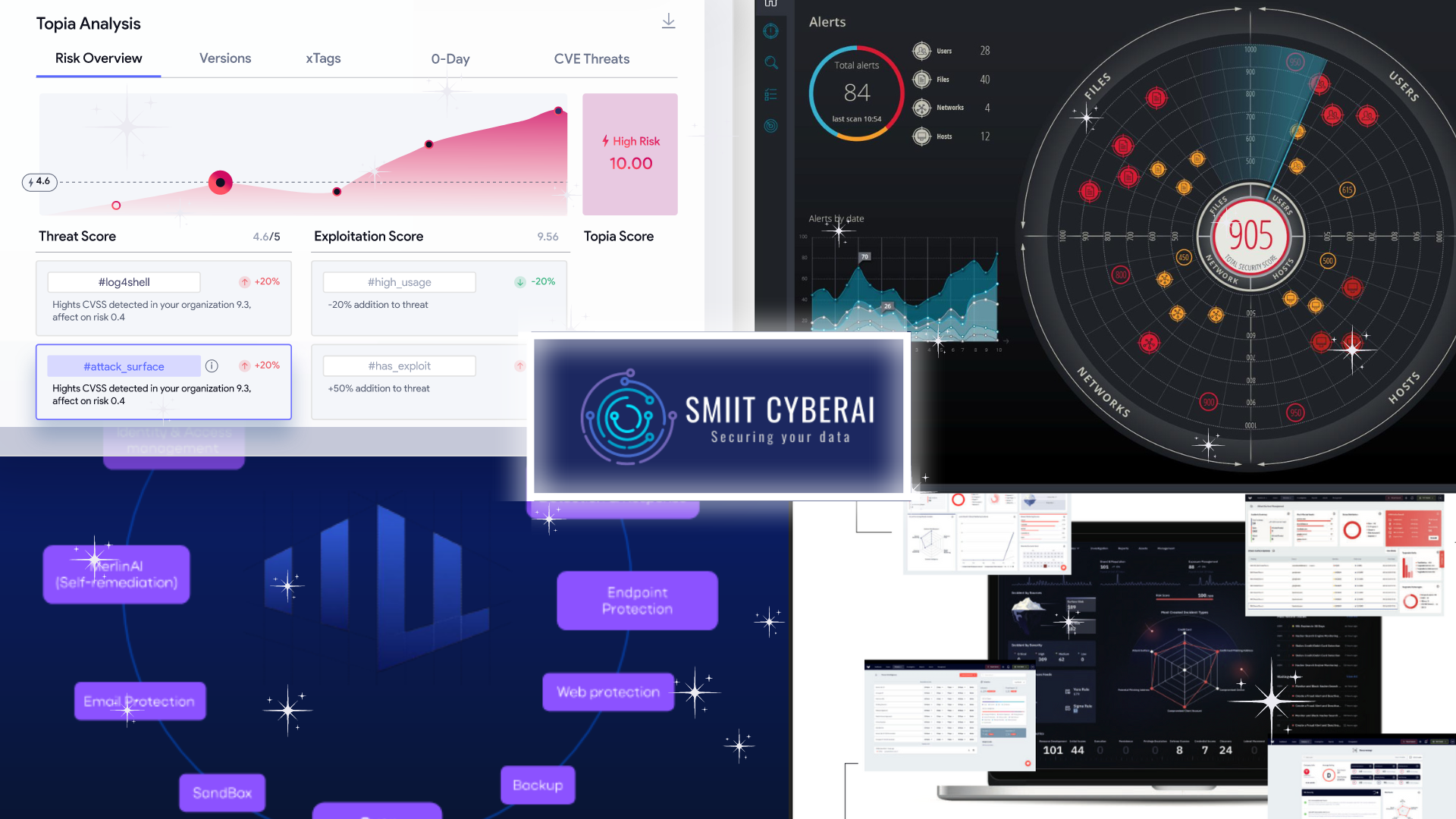
Quality Solution to Make your tech Cyber Security easier
Juggling cybersecurity for your tech devices can feel overwhelming. But fret no more! By implementing a quality antivirus solution, you can simplify your defense. These programs not only shield you from malicious software, but many also offer features like secure browsing and dark web monitoring, putting a robust shield between you and online threats.















.png)
.png)