-
Malware and Phishing Detection:
-
Security Log Analysis:
-
Endpoint Security:
-
Encryption:
-
Bias in AI Security Systems:
-
Misinterpretation:
-
Overreliance:
-
Cybersecurity Skills Gap:
-
Privacy and Legal Complications:
-
Data Unavailability and Manipulation:
-
Mitigate Bias and Misinterpretation:
-
Foster a Collaborative Approach:
-
Bridge the Skill Gap:
-
4. Prioritize Data Security and Transparency:
-
5. Continuously Learn and Adapt:
The Transformative Role of Artificial Intelligence in Cybersecurity: A Comprehensive Exploration of Key Use Cases
Introduction:
As technology advances, the landscape of cyber threats continues to evolve, resulting in an increasing number of internet-related crimes. The FBI Internet Crime Report reveals a significant surge in cybercrimes, with 847,376 complaints and financial losses exceeding 6.9 billion dollars, underscoring the critical need for robust cybersecurity measures. Organizations are increasingly turning to artificial intelligence (AI) as a pivotal component of their cybersecurity strategy to detect and counter malicious activities efficiently. In this article, we delve into the importance of AI in cybersecurity, its advantages, challenges, and real-time use cases from prominent companies such as AWS and PayPal.
The Importance of AI in Cybersecurity:
The escalating complexity of cyber threats, including phishing, scams, and data theft, necessitates innovative solutions to effectively combat these challenges. Recognizing AI's potential, 76% of enterprises prioritize AI and machine learning in their IT budgets. The sheer volume of data generated by connected devices, projected to reach 79 zettabytes by 2025, renders manual analysis impractical, making AI indispensable in the fight against cybercrime.
- Red TeamCost Reduction:
AI-driven automation streamlines routine tasks like log analysis, vulnerability assessments, and patch management, reducing the need for manual intervention and saving valuable time and resources.
Improved Scalability:
Traditional cybersecurity approaches struggle with the vast volumes of data in complex environments. AI's scalability allows it to process and analyze massive amounts of data simultaneously, ensuring proactive defense against cyber threats.
Real-Time Use Cases:
Threat Detection and Prevention:
AI systems demonstrate enhanced efficacy, surpassing legacy signature-based malware detection systems. They analyze email content, differentiate between spam and phishing attempts, and evolve to recognize sophisticated attacks like spear phishing.
AI transforms security log analysis by utilizing machine learning algorithms to detect patterns and anomalies, enabling swift identification and response to potential security breaches.
AI-driven endpoint protection takes a dynamic approach, continuously learning from network behavior to identify potential threats, including zero-day attacks, without relying on signature updates.
While encryption remains a robust defense, AI's ability to break it is challenged by the complexity of encryption algorithms like AES and SHA.
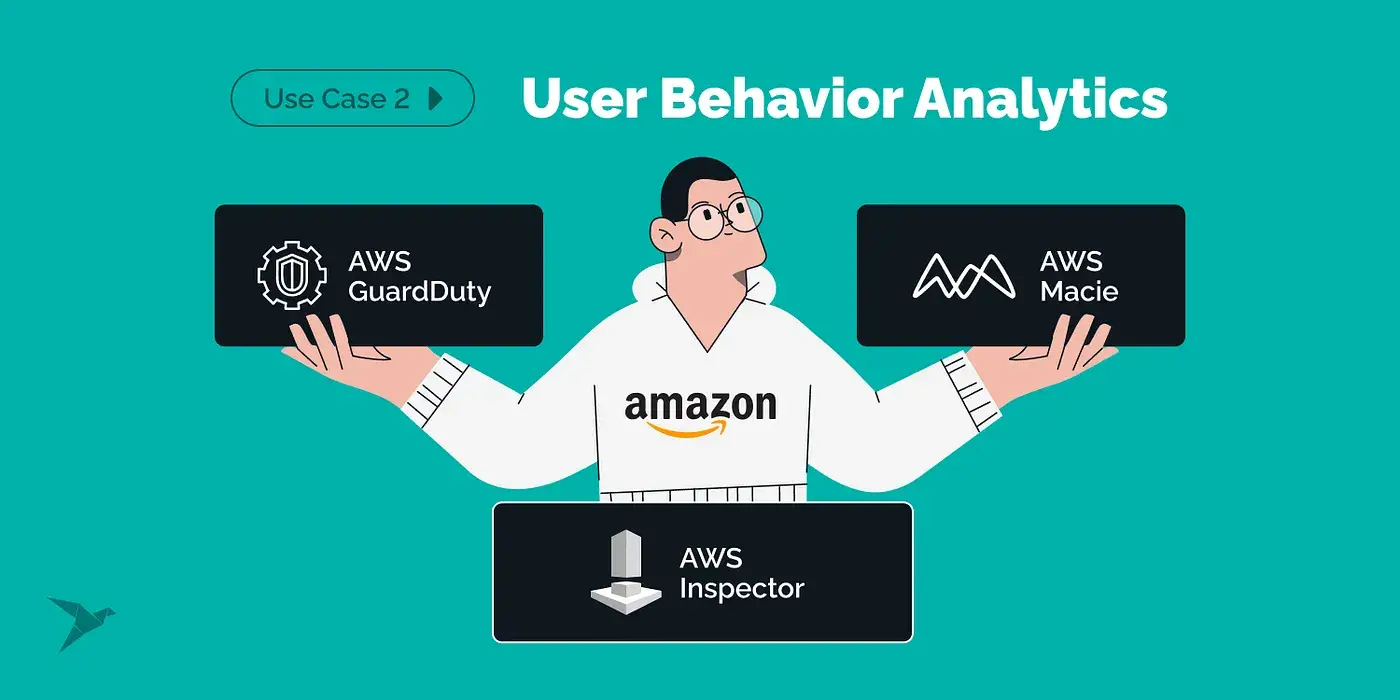
User Behavior Analytics:
User Behavior Analytics in Amazon: AWS offers AI-powered security services like GuardDuty, which analyzes various data sources to detect abnormal behavior indicating a security breach.
Advanced Threat Response and Mitigation:
Advanced Threat Response and Mitigation in Wells Fargo: Wells Fargo employs an AI-powered platform for threat detection and response, utilizing machine learning algorithms to identify patterns and anomalies in real-time.
Vulnerability Assessment and Management:
Vulnerability Assessment and Management in Splunk: Splunk's AI-driven platform prioritizes threats intelligently by analyzing data from various sources, allowing security teams to focus on addressing critical risks promptly.
Security Operations and Automation:
Security Operations and Automation in Plaid: Plaid uses advanced machine learning algorithms to analyze customer data, streamlining the onboarding process for financial institutions and enhancing overall data security.
Threat Intelligence and Predictive Analytics:
Intelligence and Predictive Analytics in PayPal: AI in PayPal's cybersecurity strategy includes transaction analysis and scanning websites for potential cyber threats, demonstrating the application of AI in predicting and preventing breaches.
Challenges of Implementing AI in Cybersecurity:
While AI offers immense potential, challenges must be addressed:
AI systems may be influenced by bias in training data, leading to discriminatory outcomes.
AI systems may misinterpret information, resulting in incorrect threat assessments and potential cybersecurity risks.
Overreliance on AI may accumulate errors, leaving organizations vulnerable to novel cyber-attacks.
The shortage of skilled professionals poses a challenge in implementing and managing AI systems effectively.
AI applications in cybersecurity may raise privacy concerns, requiring compliance with regulations and potential legal restrictions.
AI systems relying on historical data are susceptible to manipulation by malicious actors, compromising their efficiency and accuracy.
The Future of Cybersecurity and AI:
Leading tech companies, including Google, IBM, and Microsoft, are at the forefront of advancing AI systems for threat identification and mitigation. Google's Project Zero, Microsoft's Cyber Signals program, and other initiatives exemplify the commitment to enhancing cybersecurity through AI. The future of consumer cybersecurity relies on achieving a balance between the benefits and risks of AI and machine learning data-protection systems.
The Double-Edged Sword: Exploring the Potential Drawbacks of AI in Cybersecurity
Bias and Misinterpretation: AI systems can
inherit
biases from their training data, leading to
discriminatory results or misinterpreting information,
potentially overlooking real threats.
Overreliance and Vulnerability to Novel Attacks:
Overdependence on AI can create blind spots and leave
organizations susceptible to unforeseen or evolving
cyber threats requiring human expertise.
Skill Gap and Legal Hurdles: Implementing and
maintaining AI systems effectively requires a skilled
workforce, which can be scarce. Additionally, privacy
concerns and legal regulations surrounding AI use in
cybersecurity pose further challenges.
Data Manipulation and Unavailability: AI systems
relying
heavily on historical data are susceptible to
manipulation by malicious actors, compromising their
effectiveness. Additionally, limited access to relevant
data can hinder the accuracy of AI analysis.
SMIIT Cyber AI: Your Trusted Partner in a Human-Centric, AI-Powered Future of Cybersecurity.
Emphasize SMIIT Cyber AI's commitment to unbiased training data and human oversight to minimize bias and ensure accurate threat assessments.
Focus on how SMIIT Cyber AI complements human expertise, empowering security teams with AI-powered insights while emphasizing the irreplaceable role of human judgment and decision-making.
Highlight SMIIT Cyber AI's user-friendly interface and intuitive design that minimizes reliance on highly specialized expertise, making it accessible to a broader range of security professionals.
Underscore SMIIT Cyber AI's commitment to robust data security practices and transparent communication ensuring user privacy and regulatory compliance.
Emphasize SMIIT Cyber AI's continuous learning capabilities and adaptability to new threats, ensuring it remains effective against evolving cyberattacks.
Conclusion:
AI is set to play a pivotal role in the future of cybersecurity, offering unparalleled capabilities in threat detection, prevention, and response. As organizations navigate the evolving landscape of cyber threats, the continuous learning capabilities of AI models provide optimism for enhanced security, faster response times, and an adaptive defense system. Striking a balance between innovation and security is paramount in harnessing the full potential of AI in cybersecurity.
Recent Tweets
- "Protect your digital fortress! 💻🔒 Stay ahead of cyber threats with these essential cybersecurity tips" https://bit.ly/smiit-cyberai1 Jan/12/2024
- "Hackers beware! 🔍🛡️ Strengthen your defense against cyber attacks with the latest cybersecurity tools and best practices" https://bit.ly/smiit-cyberai2 Feb/10/2024







.png)




John Doe
Posted at 15:32h, 07 Jaunuary"As someone who works in the cybersecurity field, I found this blog incredibly informative! The tips on protecting against phishing attacks were especially useful. Keep up the great work, looking forward to more content like this!"
Taylor
Posted at 15:32h, 06 December"Wow, this blog opened my eyes to so many potential threats I hadn't even considered before. It's scary how vulnerable we can be online, but thanks to articles like these, I feel more empowered to take control of my digital security. Thank you for the valuable insights!"