Strengthening Your Defense Against Cyberattacks: Why VAPT Matters
Introduction:
Vulnerability Assessment and Penetration Testing (VAPT) is a powerful tool within a comprehensive cybersecurity strategy, enabling organizations to achieve this proactive approach. VAPT goes beyond traditional scanning by simulating real-world attacks on your IT systems and infrastructure. Ethical hackers employ their expertise to find and exploit vulnerabilities before malicious actors can. Through these controlled and authorized assessments, organizations can uncover security weaknesses that automated tools might miss, ultimately strengthening their defenses and protecting their digital assets.
Overview:
The digital age has opened doors for businesses, but also to a new realm of cybersecurity adversaries. These adversaries can compromise sensitive data, disrupt operations, and tarnish your reputation, leading to significant financial and reputational damage. While complying with security regulations is essential, it's crucial to move beyond compliance and adopt a proactive approach to identify and mitigate security threats before they escalate.
Why do you need Vulnerability Assessment and Penetration Testing (VAPT)?
Vulnerability Assessment and Penetration Testing are a must regardless of any type of industry your organization belongs to. It is about the verification and assessment of the security posture of your organization. In simple words, you can say that it is a method of checking whether your company is secure from outside attacks or not. In the present times, we hear a lot of hacking issues and cyber-attacks. We all need to secure our systems and networks. Doing vulnerability assessment and penetration testing will let you know the attacks and security loopholes and how to fix them.
How about businesses without a committed and efficient security measures team to deal with such vulnerabilities? SMIIT CyberAI has the ideal answer for you for that. We collaborate with the greatest cybersecurity suppliers in the world and provide a wide range of services at unbelievable costs. Our experts will be pleased to assist you if you require more than just security services. Within set timelines.
How does vulnerability assessment differ from penetration testing?
A vulnerability assessment (or vulnerability scan) is an information security process used to identify weaknesses or vulnerabilities in a computer system or network. The purpose of a vulnerability assessment is to determine the system’s vulnerabilities and help the system operator correct them.
A penetration test (or pen test) is an authorized simulated attack on a computer system performed to evaluate the system’s security. It can be described as a form of “security audit” but often implies a level of aggressiveness beyond simple audit procedures.
Why VAPT is essential for a company's privacy
Identifying Vulnerabilities:
Mitigating Security Risks:
VAPT helps in identifying vulnerabilities within a company's networks, applications, and infrastructure. By conducting thorough assessments and simulated attacks, security professionals can uncover weaknesses that could potentially be exploited by malicious actors. These vulnerabilities might include outdated software, misconfigured settings, or unpatched systems, all of which pose significant risks to the privacy of sensitive information. By identifying these vulnerabilities proactively, companies can take steps to address them before they are exploited, thereby reducing the likelihood of privacy breaches.
Through penetration testing, security teams can simulate real-world attacks to assess the effectiveness of existing security measures. By understanding how attackers might exploit vulnerabilities to gain unauthorized access to sensitive data, companies can develop and implement robust security controls and measures to mitigate these risks. This proactive approach helps in strengthening the overall security posture of the organization and ensures that privacy-sensitive information remains protected against potential threats. By regularly conducting VAPT exercises, companies can stay ahead of emerging security threats and adapt their defenses accordingly to safeguard privacy.
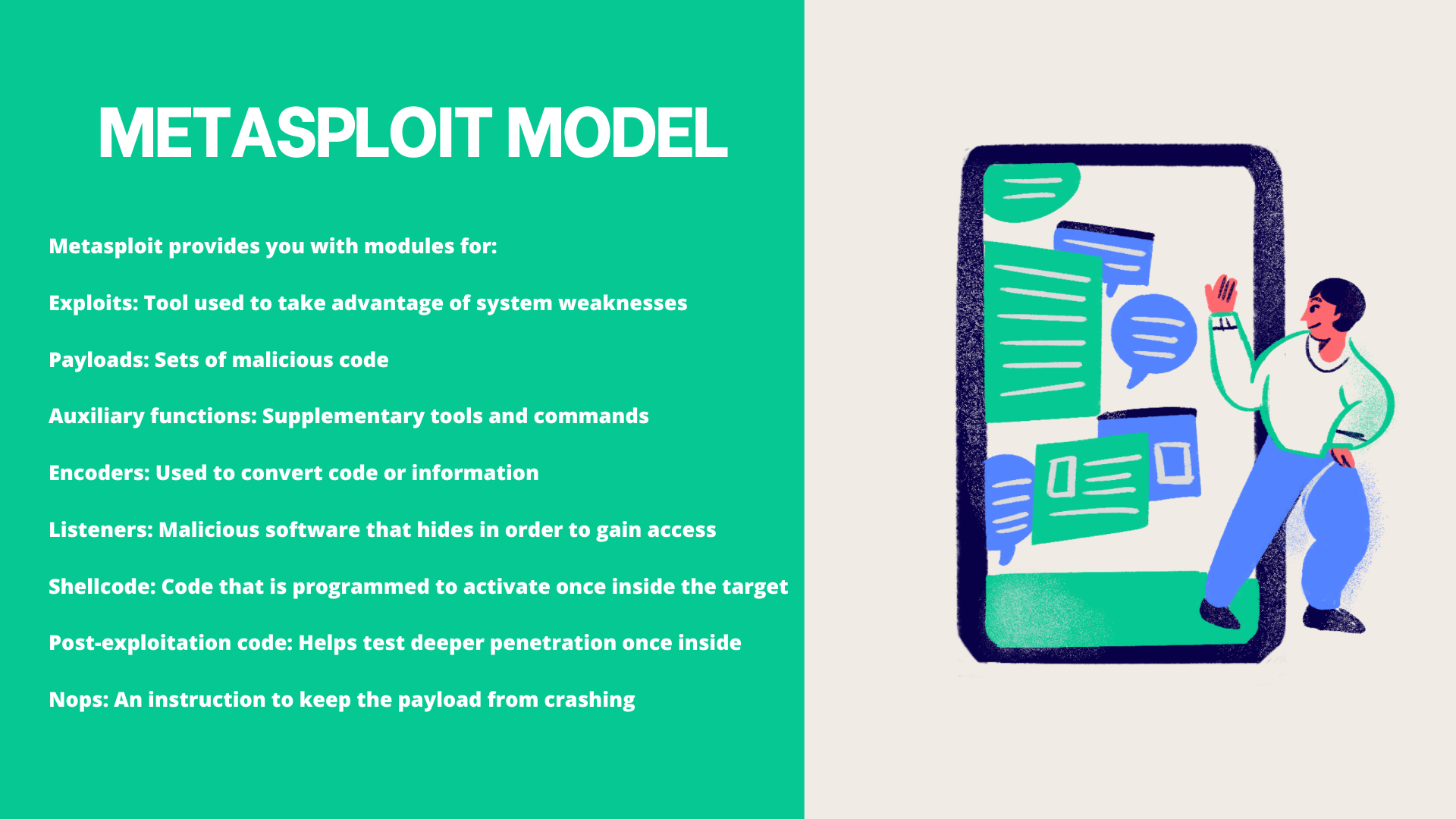
What are VAPT Tools?
VAPT tools are a
group of
software tools used to test
the
security of a system,
network,
or application.
Metasploit, a renowned
computer
security project, serves as
an
invaluable resource for both
information about security
vulnerabilities and aiding
in
penetration testing and IDS
signature development. It
stands
as an open-source, freely
accessible platform
available to
the public.
Metasploit boasts compatibility across various platforms, including Unix (encompassing Linux and MacOS) and Windows. It offers a plethora of tools designed for penetration testing, covering major protocols such as DNS, FTP, HTTP, ICMP, IMAP, IRC, TCP, and UDP. Moreover, it supports a diverse array of encodings, ranging from Unicode to ASCII, binary, hex, and more.
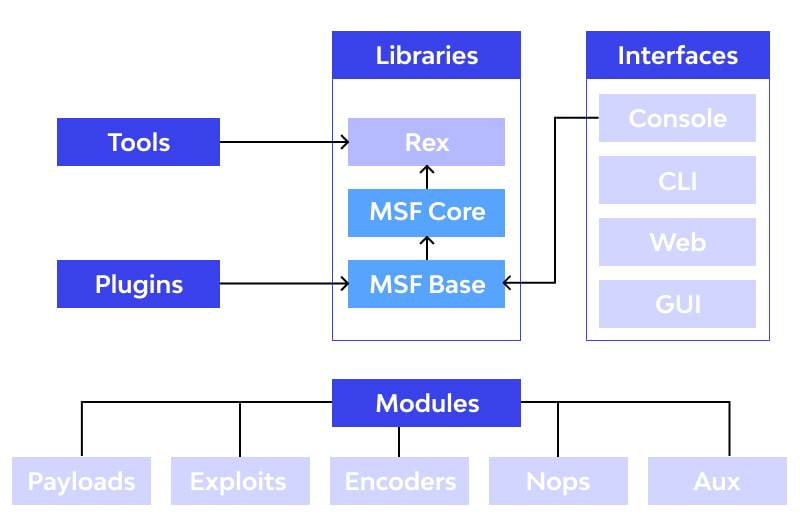
Architecture of Metasploit
The architecture of Metasploit is designed to provide a flexible and modular framework for conducting penetration testing and security assessments. Understanding its architecture is crucial for effectively utilizing its capabilities.
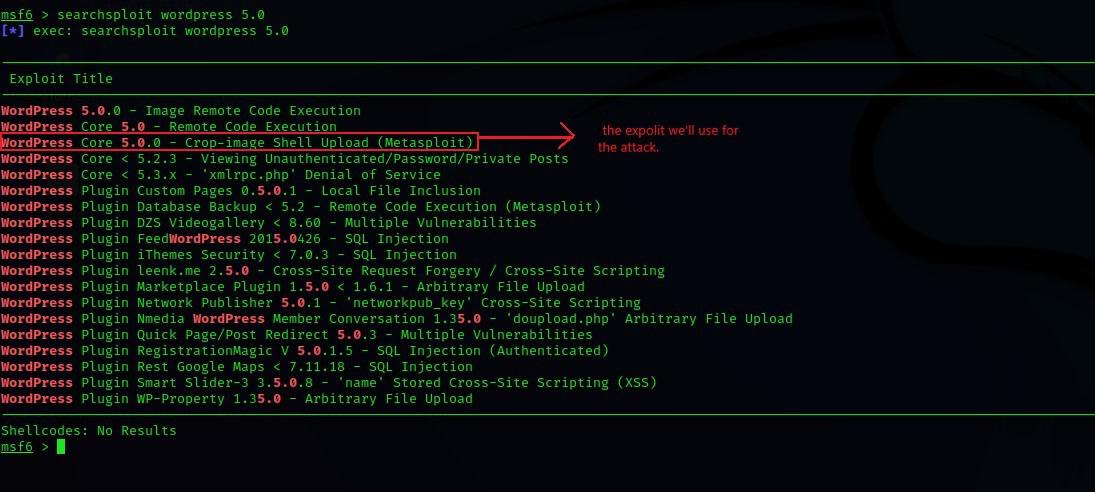
Metasploit Step-by-Step
We’ll begin a brief
tutorial
of
an easy exploit by assuming
that
you have the basic system
and OS
requirements. In order to
set up
a testing environment,
you’re
going to need to download
and
install Virtualbox, Kali,
and
Metasploitable to create a
virtualized hacking machine.
You
can download and install
Windows
XP or above in order to
create a
third virtual machine for
this
exploit.
Once you have your
testing
tools installed, you’ll
want
to open your Metasploit
console. It will look
like
this:
One shortcut is to type
“help” into the console,
which will bring up a
list
of Metasploit commands
and
their descriptions. It
should look like this:
A powerful and useful tool, to begin with, is the Armitage GUI, which allows you to visualize targets and recommend the best exploits to access them. This tool also shows advanced post-exploit functions for deeper penetration and further testing. To select it from the console, go to Applications – Exploit Tools – Armitage. Once you’ve got the form field on your screen, enter the host, port number, user ID, and password. Type ‘enter’ after all fields are completed and you’ll be ready to initiate your exploit.
Pros:
Free and Open Source:
Metasploit
is freely available to users
and
adheres to an open-source
model,
making it accessible to the
wider security community.
User-Friendly GUI
Environment:
It offers a user-friendly
graphical user interface
(GUI)
environment, enhancing
usability
and accessibility for
security
professionals.
Powerful Framework:
Metasploit
is renowned for its robust
framework, providing a
comprehensive suite of tools
and
capabilities for penetration
testing.
Assortment of Penetration
Testing Capabilities: From
reconnaissance to
exploitation,
Metasploit offers a diverse
range of penetration testing
capabilities, empowering
users
to assess and mitigate
security
risks effectively.
Cons:
Steep Learning Curve: Due to its extensive functionalities and capabilities, Metasploit may present a steep learning curve for novice users, requiring time and dedication to master. Association with Hackers: While primarily intended for legitimate security purposes, Metasploit has also been utilized by malicious hackers for unauthorized access and exploitation of systems, raising concerns about its potential misuse.
SMIIT CyberAI: Mitigating the Challenges of Cybersecurity Tools like Metasploit
Steep Learning Curve: SMIIT
CyberAI offers user-friendly
interfaces and intuitive
features that significantly
reduce the learning curve
associated with
cybersecurity
tools. Its streamlined
design
and comprehensive
documentation
make it accessible to both
novice and experienced
users,
allowing them to quickly
grasp
its functionalities and
master
its capabilities without
extensive training.
Association with Hackers:
Unlike
Metasploit, which has
unfortunately been
associated
with malicious hackers due
to
its potential for
unauthorized
access and exploitation,
SMIIT
CyberAI is developed and
maintained with a strong
emphasis on ethical usage
and
adherence to cybersecurity
best
practices. It integrates
robust
security protocols and
safeguards to prevent
misuse,
ensuring that it remains a
trusted tool for legitimate
security purposes without
compromising integrity or
ethics.
Conclusion
VAPT is indispensable for modern organizations, helping them identify vulnerabilities, mitigate security risks, and safeguard privacy-sensitive information against potential threats. With the right tools and expertise, businesses can stay ahead of emerging security challenges and ensure robust cybersecurity defenses.
Recent Tweets
- "Protect your digital fortress! 💻🔒 Stay ahead of cyber threats with these essential cybersecurity tips" https://bit.ly/smiit-cyberai1 Jan/12/2024
- "Hackers beware! 🔍🛡️ Strengthen your defense against cyber attacks with the latest cybersecurity tools and best practices" https://bit.ly/smiit-cyberai2 Feb/10/2024




.png)





John Doe
Posted at 15:32h, 07 Jaunuary"As someone who works in the cybersecurity field, I found this blog incredibly informative! The tips on protecting against phishing attacks were especially useful. Keep up the great work, looking forward to more content like this!"
Taylor
Posted at 15:32h, 06 December"Wow, this blog opened my eyes to so many potential threats I hadn't even considered before. It's scary how vulnerable we can be online, but thanks to articles like these, I feel more empowered to take control of my digital security. Thank you for the valuable insights!"