The Weakest Link: Why Supply Chain Attacks Are a Major Security Threat
Introduction:
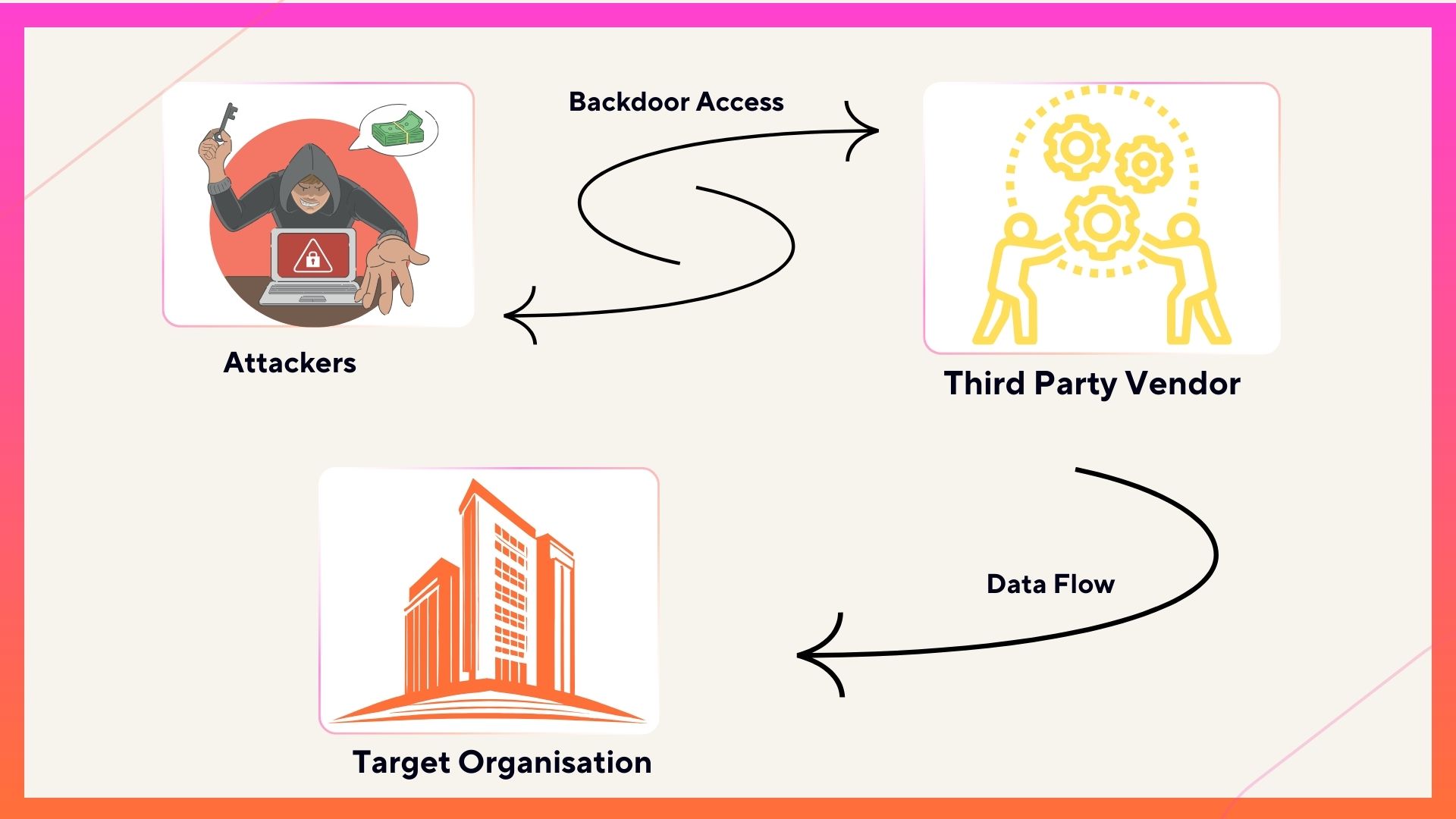
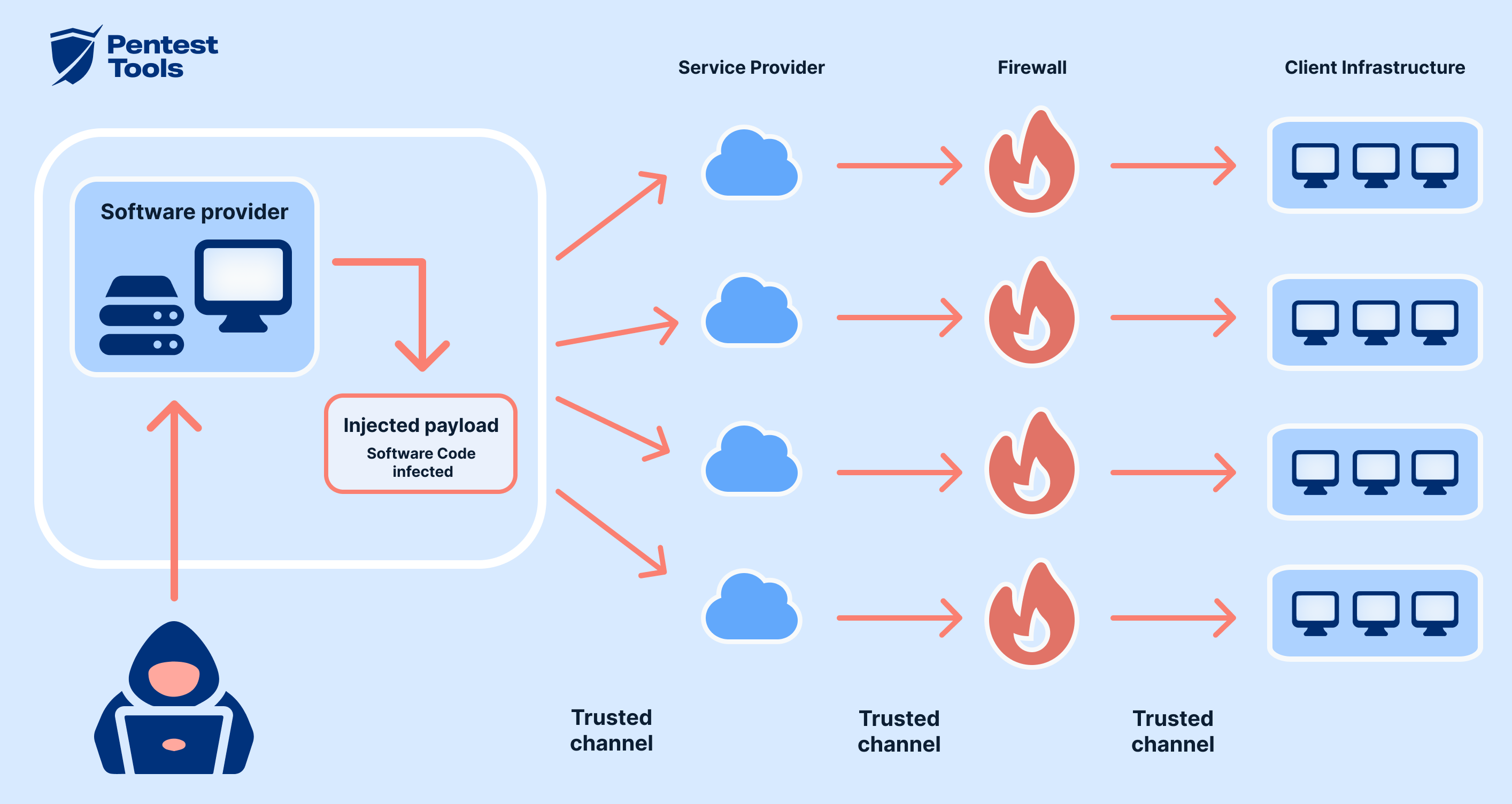
Supply chain attacks, also known as value-chain attacks or third-party attacks, exploit vulnerabilities within the interconnected network of suppliers and service providers to infiltrate organizations across various sectors. Cybercriminals strategically target these dependencies, injecting malicious code or malware into ostensibly trusted tools or services provided by third parties. By compromising these pivotal components, attackers gain surreptitious access to the systems and networks of their ultimate targets, often unbeknownst to the victims themselves. The insidious nature of supply chain attacks lies in their capacity to proliferate undetected, leveraging the trust ingrained within the fabric of interconnected supply chains. Detection proves elusive, as compromised software or hardware may evade conventional security measures, disseminating across organizational boundaries with alarming stealth. In confronting the omnipresent threat of supply chain attacks, organizations must adopt a proactive stance, bolstering resilience across their supply chain ecosystem through heightened vigilance, robust risk assessment protocols, and stringent vetting of third-party vendors to safeguard their digital infrastructure.
How Does a Supply Chain Attack Work?
Supply chain attacks are
insidious tactics that
exploit the interconnected
nature of organizational
relationships, aiming to
breach a target through
vulnerabilities in
third-party systems or
applications. These attacks
thrive on the trust
established between
organizations, leveraging
the access granted to
trusted vendors or service
providers. Even if an
organization maintains
robust cybersecurity
defenses, a compromised
third party within its
supply chain can serve as a
conduit for attackers to
infiltrate its network.
Managed service providers
(MSPs) are often prime
targets due to their
extensive access to client
networks, enabling attackers
to pivot easily and extend
the reach of their breach.
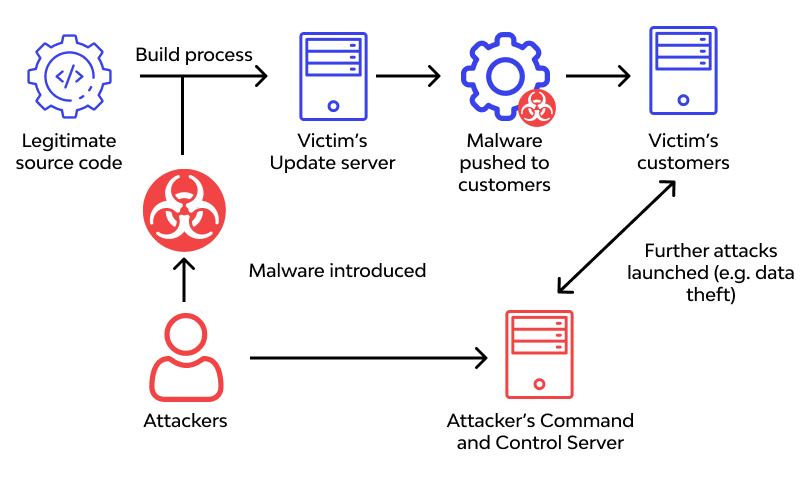
Additionally, attackers may
compromise the continuous
integration and continuous
delivery (CI/CD) pipeline in
software development,
injecting malicious code
directly into products
distributed to unsuspecting
customers.
The process typically begins
with an "upstream" attack,
where cybercriminals gain
access to a third-party
dependency through various
means such as stolen
credentials or exploiting
software vulnerabilities.
Once access is secured, the
attackers proceed with the
"downstream" attack,
targeting the ultimate
victim, often through
routine software updates or
other channels. By
exploiting weaknesses in the
supply chain, attackers can
effectively bypass the
defenses of their primary
targets, causing significant
disruption and damage.
Unveiling the Stealthy Threat: Detecting Supply Chain Attacks
The insidious breaches, while less overt than traditional cyber threats, pose a grave risk to organizations, capable of unleashing devastating data breaches and financial turmoil. So, how does one unveil these stealthy assaults before they wreak havoc? The key lies in a multi-pronged approach to detection. Vigilant monitoring of the supply chain is paramount, with continuous scrutiny of network traffic, system logs, and access patterns. Comprehensive risk assessments help identify vulnerabilities, while thorough supplier due diligence ensures the integrity of partners. Leveraging advanced analytics and threat intelligence enables organizations to detect anomalous behavior and stay ahead of emerging threats. Red team exercises simulate attacks, validating defense strategies, while collaborative partnerships foster collective defense. In the relentless battle against supply chain attacks, proactive vigilance and collaboration are the shields that fortify organizations against the lurking shadows of cyber threat.
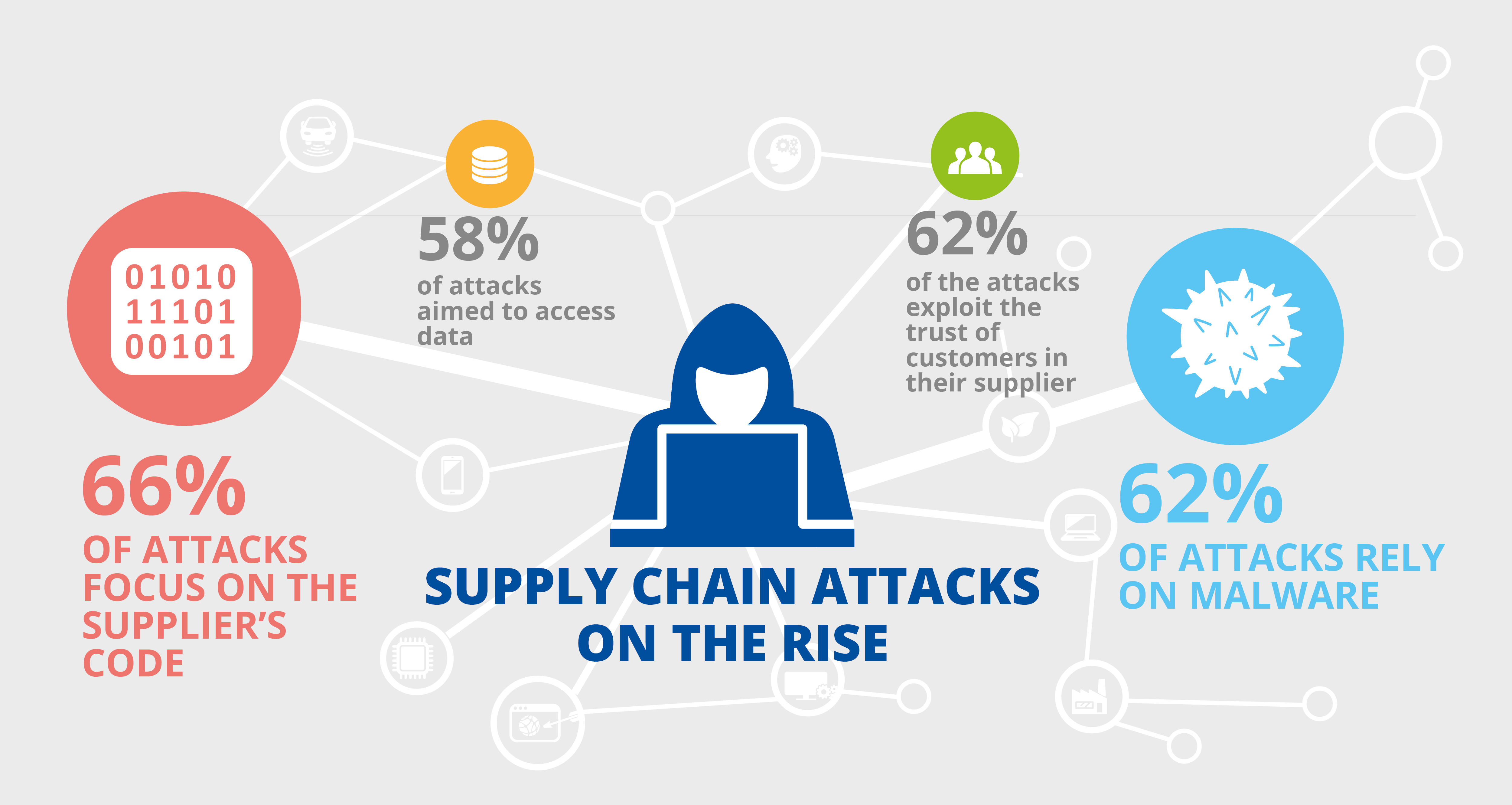
Supply Chain Attacks: Understanding Their Mechanics and Impact
Supply
chain attacks
are orchestrated with
meticulous precision. At
their core, hackers seek to
infiltrate the digital
supply chain, inserting
malicious code into software
or compromising network
protocols and components.
Once they identify a
vulnerability, they exploit
it, gaining illicit access
to critical resources.
Compounding the challenge is
the inherent trust placed in
reputable vendors. Attackers
capitalize on this trust,
often targeting products or
updates distributed by
trusted sources. Ironically,
these updates, purportedly
designed to bolster
security, may unwittingly
serve as conduits for
malicious actors.
Types of Supply Chain Attacks
Stolen Certificates:
-
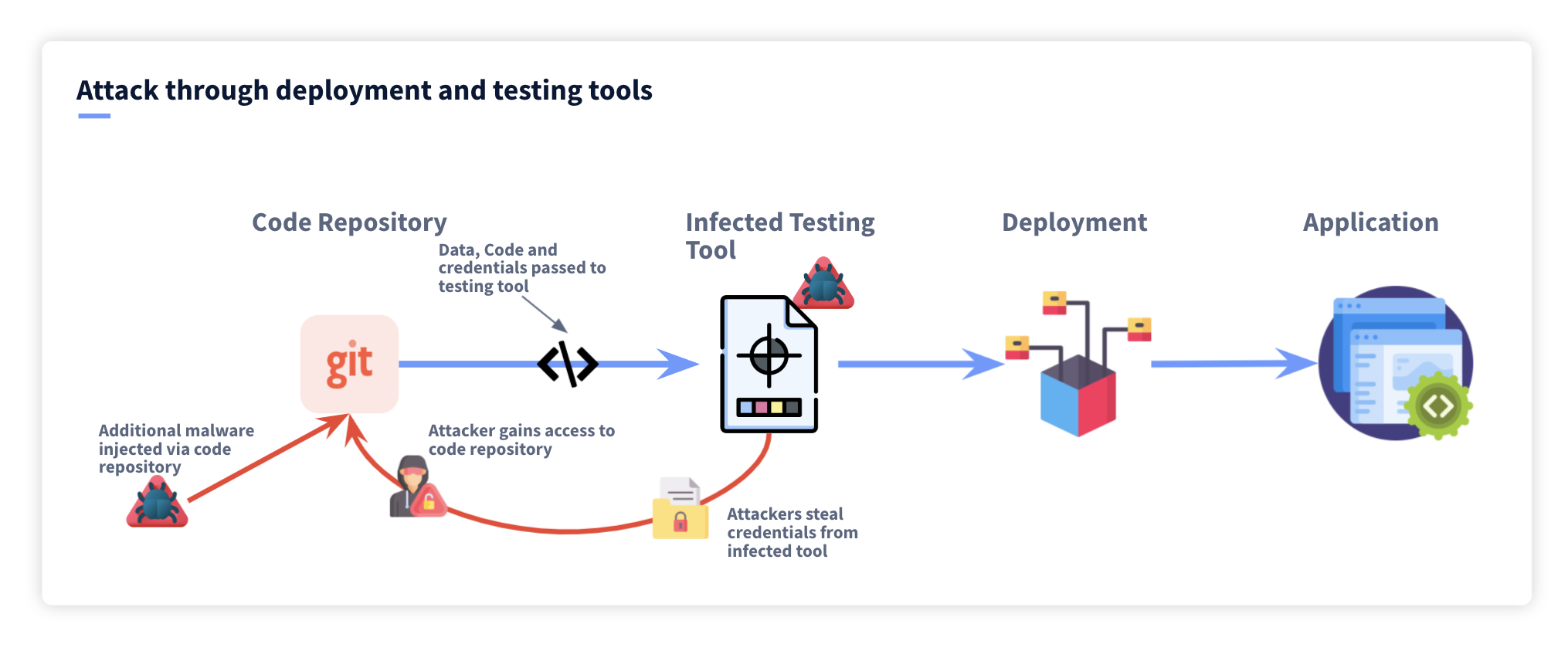
Compromised Software Development Tools:
Preinstalled Malware on Devices:
Firmware Exploitation:
Supply chain attacks
manifest in various
forms,
each leveraging
distinct
vulnerabilities:
A hacker pilfers a certificate used to validate the authenticity and safety of a company's product. With this stolen trust, they clandestinely distribute malicious code under the guise of legitimacy.
Hackers infiltrate the very tools utilized in software development, injecting vulnerabilities into the application's foundation. This subversion occurs even before the software is created, laying the groundwork for future exploitation.
Malicious
actors
embed malware
into
seemingly
innocuous
devices
such
as
phones, USB
drives,
or
cameras. When
connected
to
the target's
system
or
network, these
devices
unwittingly
introduce
malicious code,
facilitating
unauthorized
access.
Digital hardware relies on firmware to facilitate seamless operation and interaction with users and systems. Hackers exploit this dependency by implanting malicious code into firmware, enabling surreptitious access to systems or networks.
Exploring the Dynamics of Supply Chain Attacks
In
the
realm of
cybersecurity,
supply
chain
attacks have emerged
as
a
formidable threat,
showcasing the
intricate
interplay between
interconnected
organizations.
Within
this
landscape, two
predominant
forms of attacks
stand
out:
Island Hopping
Attacks
and
Supply Chain
Attacks.
Island Hopping Attacks: Navigating Through the Ecosystem
Supply Chain Attacks: Exploiting the Fabric of Trust
Navigating the Complex Terrain
Imagine
a
cybercriminal's
journey akin to
island hopping,
where they
traverse
through a
network of
interconnected
entities,
targeting
smaller
organizations to
eventually
breach
larger, more
fortified ones.
This
strategy
capitalizes
on the relative
vulnerability of
smaller entities
within the
supply
chain, serving
as
stepping stones
towards
high-value
targets.
The allure of
island
hopping lies in
its
stealthy nature.
By
exploiting the
weaker security
infrastructure
of
intermediary
organizations,
cyber
adversaries can
gradually
advance
towards their
primary
objectives.
These
intermediary
entities, often
integral parts
of
the broader
digital
ecosystem, range
from managed
service
providers to
software
vendors,
each
interconnected
through a web of
digital pathways
fraught with
vulnerabilities.
In
contrast, supply
chain
attacks operate
on a
different
premise.
Rather than
directly
targeting
vulnerabilities
within
third-party
vendors,
these attacks
manipulate
the trust
inherent
in
legitimate
business
relationships.
The
SolarWinds
cyberattack
serves as a
poignant
example, where
cyber
adversaries
infiltrated
the software
supply
chain to
propagate
malicious code,
subsequently
infiltrating
numerous
high-profile
organizations.
Unlike island
hopping
attacks, supply
chain
attacks
capitalize
on
the implicit
trust
established
between
collaborating
entities.
By breaching the
defenses of
trusted
partners,
cybercriminals
gain unfettered
access
to networks and
systems,
exploiting the
very
fabric of trust
that
underpins modern
business
operations.
As
organizations
navigate
the complex
terrain
of
supply chain
security,
understanding
these
distinct attack
vectors
is paramount.
Mitigating
the risk posed
by
island
hopping attacks
requires
fortifying the
security
posture of all
entities
within the
supply
chain,
regardless of
size.
Similarly,
combating
supply chain
attacks
necessitates a
comprehensive
reassessment of
trust
dynamics and the
implementation
of
robust
security
measures
across
all
collaborative
fronts.
In this evolving
landscape of
cyber
threats,
vigilance
and
collaboration
are
the
cornerstones of
defense.
By fostering a
culture
of proactive
security
measures and
cultivating
resilient
partnerships,
organizations
can
effectively
safeguard
against the
looming
specter of
supply
chain
attacks,
ensuring
the
integrity and
continuity
of business
operations
in an
increasingly
interconnected
world.
"Shielding Your Supply Chain: Best Practices Against Cyber Threats"
Risk Assessment and Due Diligence:
Continuous Monitoring:
Vendor Security Requirements:
Supply Chain Visibility:
Zero Trust Architecture:
Incident Response Planning:
Threat Intelligence Integration:
Employee Training and Awareness:
Continuous Improvement and Adaptation:
Collaborative Partnerships:
In today's interconnected business landscape, supply chain attacks pose a significant threat to organizations of all sizes. These clandestine assaults, often orchestrated through trusted partners or vendors, can lead to data breaches, financial losses, and reputational damage. To safeguard against this ever-looming danger, businesses must adopt a proactive and multi-layered approach. Here are some best practices to counter supply chain attacks:
Begin by conducting a thorough risk assessment of your supply chain. Identify critical vendors and assess their cybersecurity posture. Implement due diligence measures to evaluate their security practices, compliance with regulations, and track record in handling sensitive data.
Establish robust monitoring mechanisms to scrutinize the activities within your supply chain. Monitor network traffic, system logs, and access patterns for any anomalies or suspicious behavior. Real-time monitoring enables early detection and swift response to potential threats.
Define clear security requirements and expectations for vendors and third-party suppliers. Incorporate cybersecurity clauses into contracts, outlining compliance standards, data protection measures, and incident response protocols. Regularly review and enforce these requirements to ensure adherence.
Gain comprehensive visibility into your supply chain ecosystem. Map out the interconnected relationships between vendors, partners, and subcontractors. Understanding the flow of goods, services, and information enables better risk management and threat mitigation strategies.
Embrace a Zero Trust security model to mitigate the risks associated with trust assumptions within the supply chain. Adopt a least privilege approach, where access is restricted based on user identity and verified authorization. Implement robust authentication, encryption, and segmentation to limit lateral movement of attackers.
Develop and regularly update an incident response plan tailored specifically for supply chain attacks. Define clear roles and responsibilities, establish communication protocols, and conduct regular tabletop exercises to simulate attack scenarios and evaluate response readiness.
Leverage threat intelligence feeds to stay informed about emerging threats targeting supply chains. Integrate threat intelligence into security operations to enhance threat detection capabilities. Collaborate with industry peers and share threat intelligence to strengthen collective defense against evolving threats.
Invest in cybersecurity training and awareness programs for employees across all levels of the organization. Educate staff about the risks associated with supply chain attacks, phishing tactics, and social engineering techniques. Encourage a culture of security awareness and empower employees to report suspicious activities promptly.
Keep pace with evolving threats and security best practices by fostering a culture of continuous improvement. Regularly assess and update security measures, technologies, and policies to address emerging threats and vulnerabilities within the supply chain.
Forge collaborative partnerships with industry peers, government agencies, and cybersecurity communities. Participate in information-sharing initiatives, collaborate on threat intelligence sharing, and engage in joint exercises to enhance collective defense against supply chain attacks.
Strengthening Supply Chain Security with SMIIT CybeAI: A Comprehensive Solution
In today's digital landscape, where supply chain attacks loom as a persistent threat, SMIIT Cyber AI emerges as a powerful ally in fortifying organizational defenses. Through its predictive threat detection capabilities, SMIIT Cyber AI identifies potential risks within the supply chain before they materialize, offering a proactive approach to cybersecurity. Leveraging advanced behavioral analysis and anomaly detection, it continuously monitors for suspicious activity, enabling swift response and mitigation. Integrated with real-time threat intelligence feeds, SMIIT Cyber AI adapts to evolving threats, ensuring up-to-date protection against emerging attack vectors. With its user-friendly interface and actionable insights, it empowers security teams to make informed decisions and take proactive measures. Scalable and adaptable, SMIIT Cyber AI caters to organizations of all sizes, providing seamless integration and rapid deployment. In the battle against supply chain attacks, SMIIT Cyber AI stands as a beacon of resilience, offering unparalleled protection and peace of mind.
Recent Tweets
- "Protect your digital fortress! 💻🔒 Stay ahead of cyber threats with these essential cybersecurity tips" https://bit.ly/smiit-cyberai1 Jan/12/2024
- "Hackers beware! 🔍🛡️ Strengthen your defense against cyber attacks with the latest cybersecurity tools and best practices" https://bit.ly/smiit-cyberai2 Feb/10/2024




.png)