Secure Your Digital Citadel: A Comprehensive Guide to Cybersecurity
Introduction:
In this age where technology reigns supreme, the need for cybersecurity transcends mere choice; it is a burning imperative. The digital realm, vast and ever-expanding, is a perilous landscape teeming with evolving threats, ever ready to breach our defenses. To navigate this treacherous terrain, a proactive approach is key. We must remain keenly vigilant, our eyes peeled for the slightest hint of danger. Robust security practices are our armor, the unyielding shield that protects our digital sanctuaries. As we traverse the uncharted territories of the digital age, safeguarding our digital fortresses becomes paramount. Let us raise our flaming swords of cybersecurity and stand united against the ever-present forces of cyber threats!
The Alarming Surge in Cybercrime
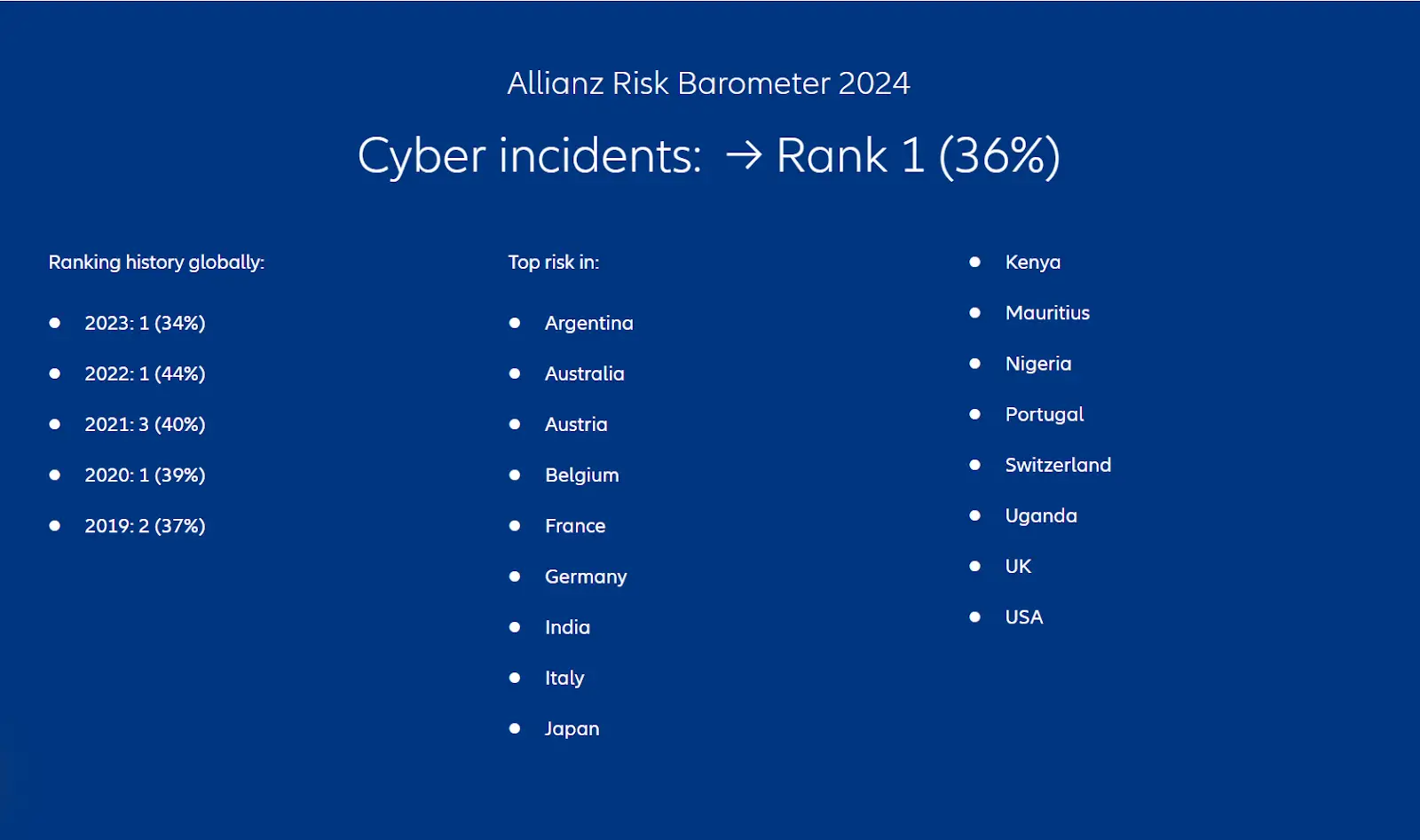
Recent years have witnessed an alarming surge in cybercrime rates, with a staggering 300% increase since the onset of the COVID-19 pandemic. In the United States alone, the average cost of a data breach is a daunting $9.44 million, and the projected global cost of cybercrime is expected to reach a staggering $8 trillion by 2023. Perhaps even more concerning is the fact that 95% of data breaches are attributed to human error.
- Red TeamUnveiling the Tactics: Social Engineering and Phishing
Social engineering tactics have emerged as a primary method for cybercriminals to obtain sensitive employee data and credentials. Shockingly, over 75% of targeted cyberattacks initiate with a deceptive email. Enter phishing, the ubiquitous cybercrime that ensnares users through deceitful messages, initiating more than 90% of all cyber attacks.
Every 39 Seconds: The Reality of Cyber Attacks
Picture this: around 2,200 cyber attacks per day, or approximately one attack every 39 seconds. This relentless onslaught underscores the urgency for individuals and organizations alike to fortify their digital defenses against a myriad of cyber threats.
Building Your Digital Bastion:
Now, let's delve into the proactive measures essential for protecting your digital identity:
Use Strong Passwords:
Employ complex passwords incorporating letters, numbers, and symbols. Steer clear of password reuse across multiple platforms.
Multi-Factor Authentication (MFA):
Implement MFA, a security tool demanding users to authenticate through multiple verification methods.
Device Vigilance:
Ensure your devices are locked after periods of inactivity. Activate location tracking for lost or stolen devices.
Record Serial Numbers:
Maintain a record of serial numbers for crucial devices to facilitate recovery in case of theft.
Credit Monitoring:
Freeze your credit to thwart fraudsters. Regularly monitor credit reports for any suspicious activities.
Secure Connectivity:
Utilize secure Wi-Fi or a Virtual Private Network (VPN) to protect your online activities.
Regular Updates and Backups:
Keep devices and software updated, and invest in a robust security and identity protection solution.
Additional Layers of Defense
-
Safeguard Your Social Security Number:
-
Automatic Security Software Updates:
-
External Data Storage:
-
Encrypted Connections:
-
Diligent Password Practices:
-
Social Media Vigilance:
Beyond the fundamental measures, consider these
supplementary strategies to bolster your digital
defenses:
Limit the use of your Social Security number and keep your card in a secure place.
Ensure your security software, operating systems, browsers, and apps are regularly updated.
Back up essential data on an external drive and store hard copies in a secure location.
Prioritize encrypted websites for online transactions and exercise caution on public Wi-Fi networks.
Regularly update passwords, avoid reuse, and create robust combinations.
Exercise discretion on social media, avoiding oversharing and limiting personally identifiable information.
Navigating the Challenges: "Cons"
-
Overwhelming Complexity:
-
Resource Intensiveness:
-
Potential User Resistance:
-
Limited Coverage of Emerging Threats:
-
Dependence on Human Compliance:
-
Complexity of Implementation:
Addressing these cons requires a balanced approach that
considers the unique needs, resources, and capabilities
of individuals and organizations while striving to
maintain effective cybersecurity practices
Implementing numerous security measures outlined in the guide might overwhelm users unfamiliar with cybersecurity practices.
Many recommended practices demand significant time, effort, and financial resources to implement and maintain.
Users may resist adopting stringent security measures due to perceived inconvenience or complexity.
The guide may not cover the latest trends or emerging threats, leaving users vulnerable to novel attack methods
Human error remains a significant contributor to breaches despite technological safeguards.
Certain measures require technical expertise beyond average users, hindering successful implementation
SMIIT CYBER AI: Your Solution to Cybersecurity Guide's Challenges
SMIIT CYBER AI empowers users to overcome the
challenges outlined in the cybersecurity guide by
providing innovative solutions that enhance security
posture, streamline operations, and adapt to the
evolving threat landscape
SMIIT CYBER AI offers a comprehensive solution to the
challenges posed by cybersecurity complexities. It
simplifies intricate processes, optimizes resources, and
promotes user acceptance through intuitive interfaces.
With constant monitoring and proactive alerts, it
ensures vigilance against emerging threats while
minimizing human error through automated protocols.
SMIIT CYBER AI provides cost-effective solutions
tailored to diverse needs and budgets, ensuring
affordability without compromising effectiveness. Its
guided implementation and robust support make adoption
and maintenance simple, empowering users to navigate the
digital landscape securely and confidently.
Conclusion:
In navigating the digital landscape, knowledge is power. By staying informed and implementing these recommended strategies, you can traverse the digital frontier with confidence, secure in the knowledge that your digital assets are shielded against the relentless evolution of cyber threats in the modern age.
Recent Tweets
- "Protect your digital fortress! 💻🔒 Stay ahead of cyber threats with these essential cybersecurity tips" https://bit.ly/smiit-cyberai1 Jan/12/2024
- "Hackers beware! 🔍🛡️ Strengthen your defense against cyber attacks with the latest cybersecurity tools and best practices" https://bit.ly/smiit-cyberai2 Feb/10/2024




.png)




John Doe
Posted at 15:32h, 07 Jaunuary"As someone who works in the cybersecurity field, I found this blog incredibly informative! The tips on protecting against phishing attacks were especially useful. Keep up the great work, looking forward to more content like this!"
Taylor
Posted at 15:32h, 06 December"Wow, this blog opened my eyes to so many potential threats I hadn't even considered before. It's scary how vulnerable we can be online, but thanks to articles like these, I feel more empowered to take control of my digital security. Thank you for the valuable insights!"