Stop Data Breaches Before They Start: OWASP Tools You Need
Introduction:
The Open Web Application Security Project, or OWASP, is an international non-profit organization dedicated to “web application security”. One of OWASP’s core principles is that all of their materials be freely available and easily accessible on their website, making it possible for anyone to improve their own web application security. The materials they offer include documentation, tools, videos, and forums.
Why do you need OWASP?
Injection Attacks:
Broken Authentication:
Sensitive Data Exposure:
XML External Entities (XEE):
Broken Access Control:
Security Misconfiguration:
Cross-Site Scripting (XSS):
Insecure Deserialization:
Using Components With Known Vulnerabilities:
Insufficient Logging And Monitoring:
Untrusted data sent to code interpreters can lead to SQL injection attacks, compromising data integrity and security.
Vulnerabilities in login systems can grant attackers unauthorized access to user accounts, potentially leading to system compromise.
Failure to protect sensitive data such as financial information can result in unauthorized access and exploitation by malicious actors.
Exploiting vulnerabilities in XML parsers can allow attackers to access sensitive data or execute unauthorized actions.
Flaws in access control mechanisms may enable attackers to perform actions reserved for privileged users without proper authorization.
Default configurations and verbose error messages can expose vulnerabilities and increase the risk of exploitation.
Allowing users to inject custom code into web applications can lead to the execution of malicious scripts in other users' browsers.
Deserializing data from untrusted sources can result in serious consequences such as DDoS attacks and remote code execution.
Vulnerabilities in third-party components can be exploited to compromise web applications, emphasizing the importance of patching and updates.
Inadequate detection of data breaches can prolong the time it takes to discover and respond to attacks, giving attackers ample opportunity to cause damage.
OWASP Projects:
OWASP is a community of
developers, technologists and
evangelists improving the
security of software. The OWASP
Foundation gives aspiring open
source projects a platform to
improve the security of software
with:
Visibility:
Credibility:
Resources:
Community:
Our website gets more than six million visitors a year
is well known in the AppSec community
and Project Summits are available for qualifying Programs
Conferences and Local Chapters connect Projects with users
The best project so far has been “OWASP Application Security Verification Standard"
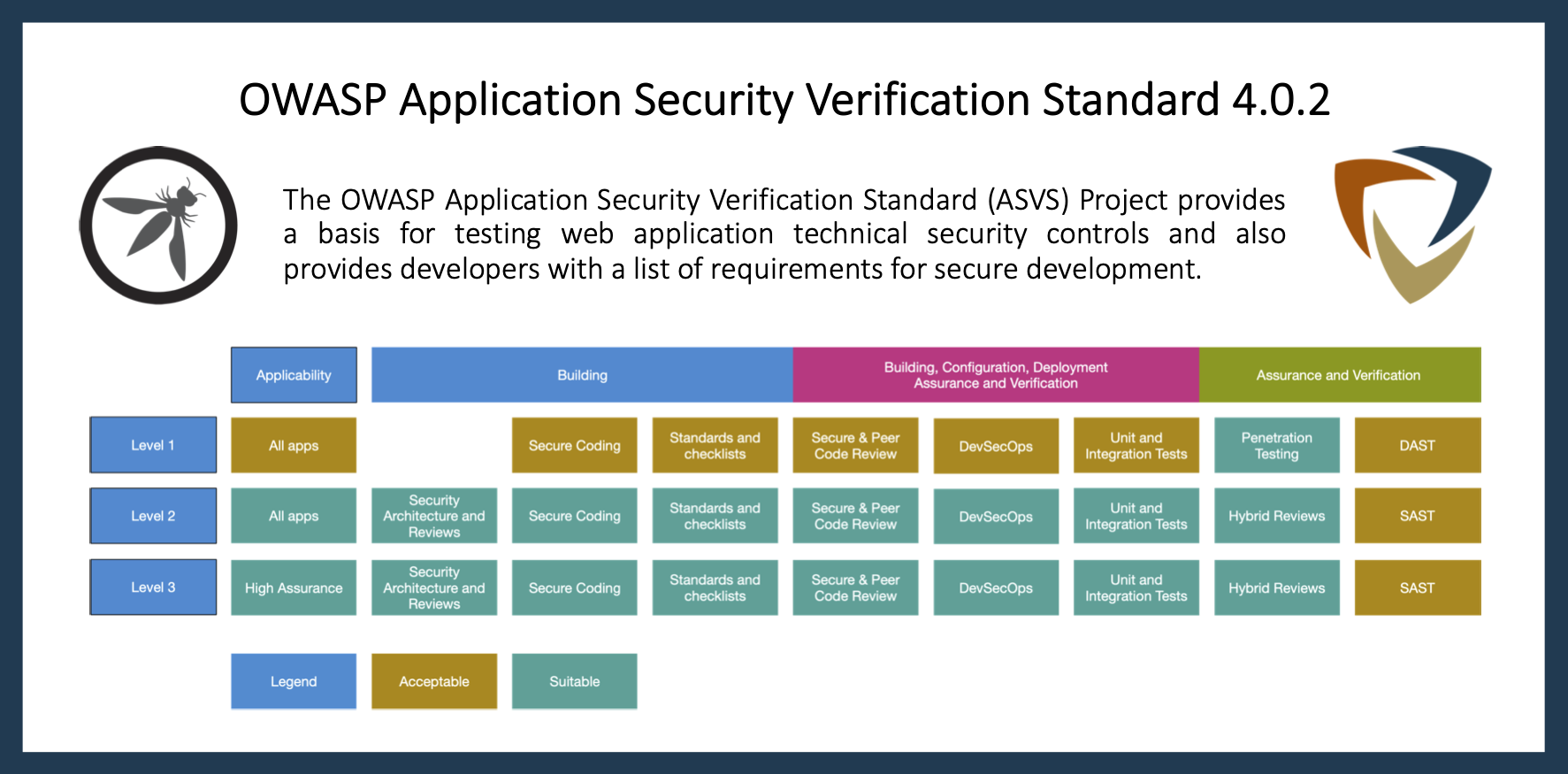
The OWASP Application
Security Verification Standard
(ASVS) Project provides a basis
for testing web application
technical security controls and
also provides developers with a
list of requirements for secure
development.
The primary aim of the OWASP
Application Security
Verification Standard (ASVS)
Project is to normalize the
range in the coverage and level
of rigor available in the market
when it comes to performing Web
application security
verification using a
commercially-workable open
standard. The standard provides
a basis for testing application
technical security controls, as
well as any technical security
controls in the environment,
that are relied on to protect
against vulnerabilities such as
Cross-Site Scripting (XSS) and
SQL injection. This standard can
be used to establish a level of
confidence in the security of
Web applications
Don't let security gaps compromise your web application's success.
OWASP Zapacts as your
automated security watchdog,
constantly scanning and alerting
you to potential problems
OWASP ZAP, a free and
easy-to-use tool, empowers you
to shield your website from
common threats like compromised
logins, data breaches, and
malicious code injections.
It automatically scans your
application, identifies
vulnerabilities, and alerts you
to potential issues, allowing
you to fix them before they
become a problem
It checks for weak
authentication, exposed data,
and malicious code like SQL
injection and XSS. With a
growing community of developers
constantly improving the tool.
Let’s see one of the core Feature of Zap i.e : Zap Authentication Most apps protect their main functionality using authentication. If you cannot authenticate to the app then you will not be able to find the most interesting and impactful vulnerabilities. Unfortunately authentication is hard, especially as there are so many different ways that apps handle authentication.
Authentication
Authentication and Testing Environment:
Disabling Security Controls:
Simplifying Authentication for Testing:
Using ZAP Desktop for Testing:
Authentication restricts access
to the application and
complicates testing tools like
ZAP, even for authorized users.
Testing with valid credentials
in a production environment
risks data pollution and service
disruption.
In a safe testing environment, security controls like firewalls should be disabled to focus solely on testing the application functionality.
If possible, disable or simplify
authentication mechanisms during
testing to focus on app
functionality rather than
authentication controls.
Simplified authentication
methods like HTTP auth or POST
forms are easier to set up and
less likely to interfere with
testing.
Consider the complexity of
authentication mechanisms like
Single Sign-On (SSO) or Two
Factor Authentication (2FA) and
their impact on automated
testing.
While automation may require authentication, testing in the ZAP Desktop provides visibility into requests and responses, facilitating real-time adjustments for effective testing.
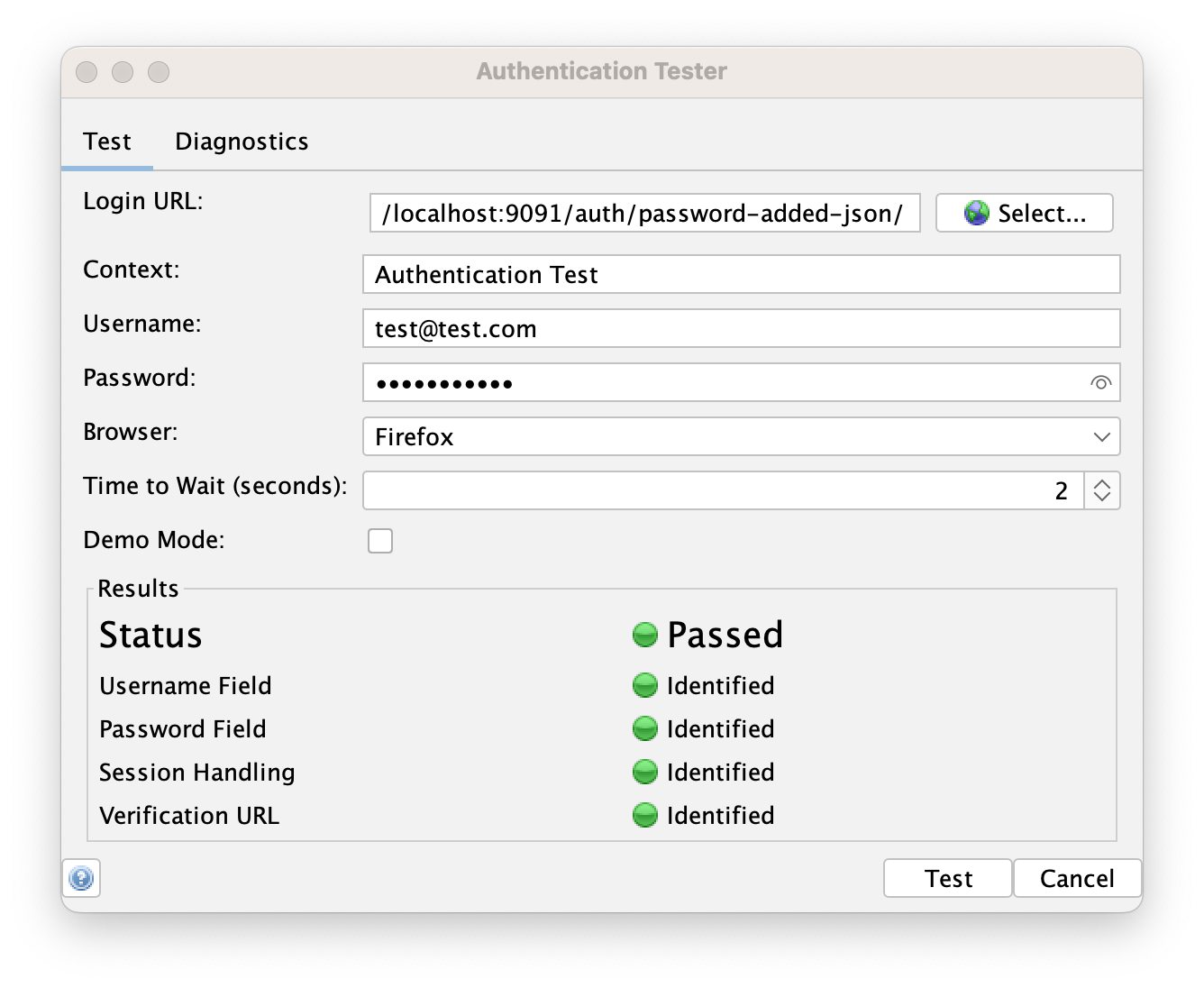
Authentication Tester Dialog
The Authentication Tester Dialog is a quick and easy way to check if ZAP can automatically detect all of the information it needs - you only need to provide the URL of your login page and valid credentials.
Auto Detection in the Desktop
The Authentication Tester Dialog will automatically create a new Context for you (by default “Authentication Test”). This will be updated with the details that ZAP detects.
Auto Detection in the Automation Framework
Contexts:
Sessions Handling:
Credentials:
Verification Strategies:
You can use authentication
auto-detection in an Automation
Framework plan by configuring the
environment
Organization: ZAP contexts serve as structural units grouping related URLs, typically corresponding to distinct web applications, facilitating organized testing approaches.
Authentication Binding: Sessions in ZAP facilitate the binding of user authentication credentials to their HTTP traffic, ensuring secure and accurate testing by understanding and managing session IDs or tokens.
User Authentication Data: ZAP requires access to user credentials, including user identifiers and private information, to authenticate during testing sessions and perform actions within the application.
Continuous Authentication Monitoring: ZAP employs verification strategies to monitor the authentication status of users throughout testing sessions, automatically re-authenticating if sessions expire or become invalidated, ensuring consistent and accurate testing results.
Though it has so much of Pros, There are some Cons of OSWAP ZAP:
Outdated UI that can sometimes be
clunky and may require some
customization before it is
comfortable.
Automated scanning capabilities
are
limited compared to other tools
Complicated to use for novice
users.
There is no web version.
You
have to
download it into your system to
use
it.
Documentation is rough and
difficult
to understand.
Don't Worry, We've Got You Covered
While OWASP ZAP offers valuable
tools and resources, it may not be
the perfect solution for everyone.
Here at SMIIT Cyber AI, we
understand the challenges and
complexities of web application
security
Here's where we come in:
We offer comprehensive web
application security services,
including vulnerability assessments,
penetration testing, and ongoing
monitoring.
Our team of experienced
professionals can help you address
the limitations of OWASP ZAP, such
as the outdated UI and limited
automated scanning capabilities.
We provide user-friendly solutions
and clear communication, making
security accessible even for
individuals less familiar with the
technical aspects.
Leave the complexities of web
security to us and focus on
building your business with
confidence.
Conclusion
The Open Web Application Security Project (OWASP) stands as a vital pillar in the realm of web application security, offering freely accessible resources, community-driven projects, and standardized frameworks such as the OWASP Application Security Verification Standard (ASVS). OWASP ZAP (Zed Attack Proxy) emerges as a formidable tool for automated security testing, particularly in authentication testing where it enables the identification and mitigation of vulnerabilities like weak authentication and data exposure. With its emphasis on structured testing approaches through contexts and meticulous session handling, ZAP empowers developers to safeguard their applications against a myriad of threats. Together, OWASP and ZAP serve as guardians of web application integrity, enabling developers to fortify their systems and mitigate security risks proactively.
Recent Tweets
- "Protect your digital fortress! 💻🔒 Stay ahead of cyber threats with these essential cybersecurity tips" https://bit.ly/smiit-cyberai1 Jan/12/2024
- "Hackers beware! 🔍🛡️ Strengthen your defense against cyber attacks with the latest cybersecurity tools and best practices" https://bit.ly/smiit-cyberai2 Feb/10/2024

.png)
.png)


.png)





John Doe
Posted at 15:32h, 07 Jaunuary"As someone who works in the cybersecurity field, I found this blog incredibly informative! The tips on protecting against phishing attacks were especially useful. Keep up the great work, looking forward to more content like this!"
Taylor
Posted at 15:32h, 06 December"Wow, this blog opened my eyes to so many potential threats I hadn't even considered before. It's scary how vulnerable we can be online, but thanks to articles like these, I feel more empowered to take control of my digital security. Thank you for the valuable insights!"